Crunchyroll incident post mortem
On November 4, 2017, Crunchyroll suffered an attack, which hijacked their website and redirected visitors to a fake web page with a malicious file. In this post, I’ll share the details of this incident from my point of view.
Background
I’ve been developing a desktop application called Taiga, since 2008. It allows users to manage their anime libraries and keep track of their progress as they watch new episodes. It supports detection of media players and official streaming sites, including Crunchyroll.
Because it’s free software, anyone can modify and redistribute copies of Taiga. Attackers behind this incident did just that, likely to make their malware look somewhat legitimate. The result is CrunchyViewer.exe, which is basically part-Taiga, part-virus. This file was distributed over Crunchyroll’s website during the attack:

Efforts
The incident was first brought to my attention with a tweet. I opened an issue at GitHub right after confirming it (the first post has since been updated), and spent the entire day following the developments.
Around the time Crunchyroll’s website got back to normal, I got the idea of deploying a targeted update to infected machines, using Taiga’s auto-update mechanism. In order to get confirmation about the disinfection process, I reached out to malware researcher Bart Blaze, who had written a detailed analysis of the malware. After that, I was able to deploy the fix as planned. It wasn’t as effective as I hoped, because the spread had since slowed down and the fix required users to run the malicious file again. Still, this targeted update apparently fixed 41 computers, which is better than nothing.
On November 5, 2017, I contacted Ellation, the parent company of Crunchyroll. They forwarded me directly to their CTO, Simon Obstbaum, who said he’d be happy to look into my findings, and asked if I preferred sharing them over email or a call. Next day, I sent an email including my findings below, with additional details and suggestions. I don’t know if there’s an ongoing investigation. Despite my follow-up questions and delaying this write-up for over a month, I haven’t heard anything from them since then.
Findings
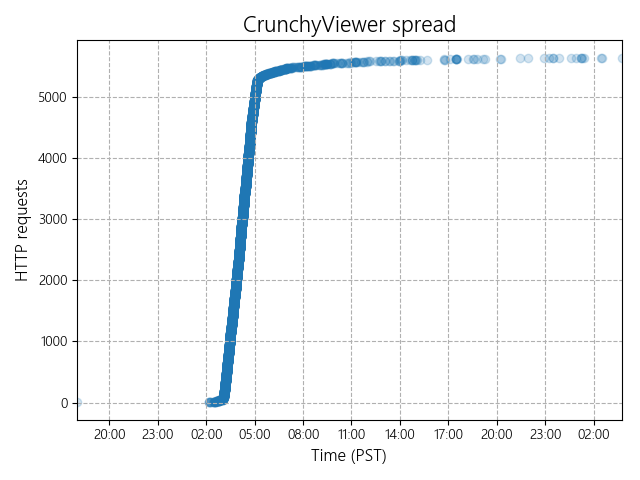
The primary source of information for me was the logs on my server. CrunchyViewer.exe uses Crunchyroll/1.3 (rather than the usual Taiga/1.x) as its user-agent string. With that in mind, I was able to plot a chart to see how fast the malware spread. Note that each dot corresponds to an HTTP request made by CrunchyViewer.exe at startup to check for application updates:
My logs don’t quite match the timeline Ellation provided in their blog post:
- 3:30am PST: Cloudflare configuration is changed
- 6:00am PST: Site is taken down
- 9:00am PST: Cloudflare configuration is restored
- 9:30am PST: Crunchyroll service is fully restored
In my logs, I see the first victim at . The spread speeds up at ~3:00am PST (DNS propagation?), and then slows down at ~5:00am PST (site taken down?). Within 24 hours, 3969 unique IP addresses are affected (some of these belong to security researchers and automated tools).
If you take a careful look at the chart, you’ll see a dot at the previous day. This is prior to the attack, so it most likely belongs to the culprit. WHOIS lookup reveals that the IP address belongs to a telecom company in Canada.
Digging deeper in the server logs, I find that this person first arrived at Taiga’s website on from google.ca (again, Canada). They downloaded Taiga’s setup, but didn’t run it. After a while, they ran the beta version of Taiga (from the development branch of its GitHub repository) a dozen times. They didn’t enter a MyAnimeList username. In their final HTTP request, the application’s user-agent string changed from Taiga/1.3 to Crunchyroll/1.3.
Speaking of Canada, source code of the fake HTML page displayed during the attack contains the string, “Your detected location is Canada.” This is a static page, which means that the original dynamic one was scraped by someone with an IP address from Canada.
I examined the contents of CrunchyViewer.exe to some extent. From what I can tell, it’s based on this git commit of Taiga. It’s dated , so they must have cloned it (or pulled the changes) at a later time, within the following couple of days before the attack. GitHub’s clone graph shows a number of clones around that time, but doesn’t give any details.
CrunchyViewer.exe also includes a reference to C:\Users\Ben\Desktop\taiga-develop\bin\Debug\Taiga.pdb, which indicates that the file was compiled on a Windows system with the username of “Ben”.
Afterword
On the day of the attack, I tried focusing on preventing the spread and cleaning the infected machines. But the whole thing was an unpleasant experience for me, in many ways.
Seeing that the malicious file had links to Taiga, some people put two and two together, and accused me of being the culprit. On the other hand, some people showed their support, and some even joked, “Taiga is so good, even the malware developers are using it.” Not sure if I should feel proud.
Above all, there are two things that affected me the most. The first was seeing a project I spent years working on, being used as a disguise. The fact that I was aware misuse could always happen didn’t quite help when it actually happened. It triggered a “how dare you” response in me, which motivated me to fight back. The second was checking out my server logs and watching more and more computers being infected in real-time. I couldn’t help imagining the people behind those numbers, getting confused, frustrated, worried…
If I had to speculate, the attack looked like an attempt to discredit Crunchyroll rather than a means to spread malware. It’s easy to blame Crunchyroll over their poor security practices, and their users have the right to do so. I must say, their lack of response also left me unimpressed. Here’s hoping they’ve learned from their mistakes. Without security, there’s one less reason to choose official streaming services over unofficial ones.